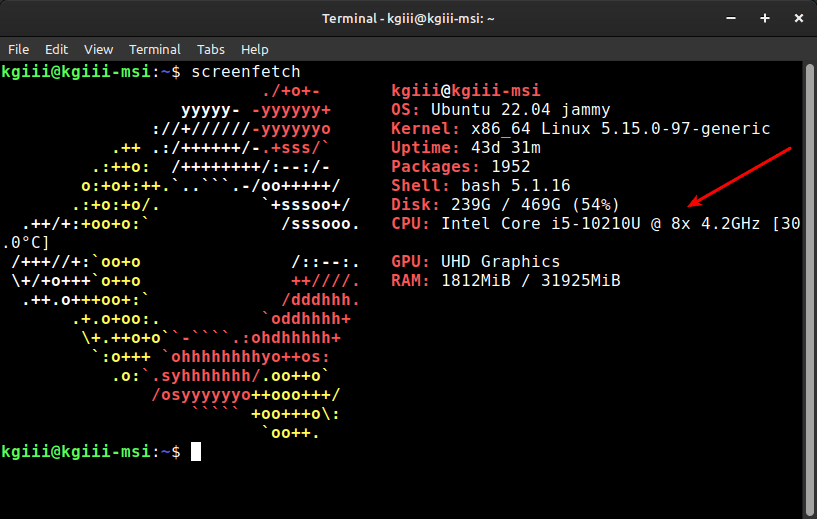
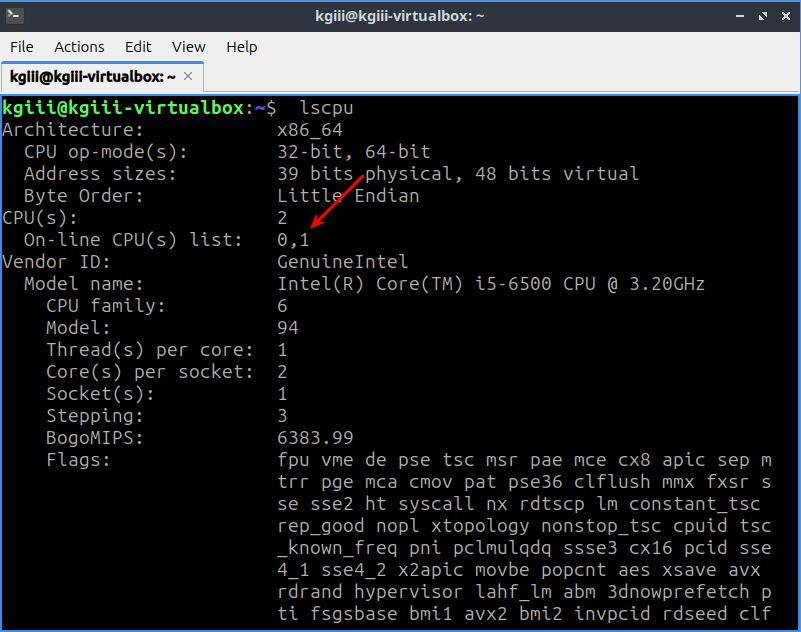
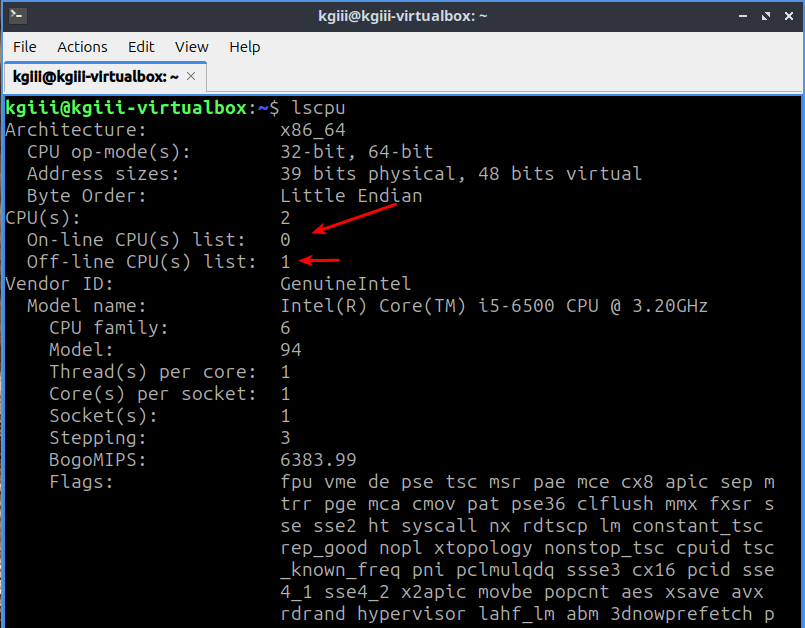
I have not done a meta article lately. I don’t find them interesting to write even though people seem to show some interest in them. They’re a pain to write and I can write a regular article easier than a meta article.
After all, my normal meta article is just updating you on how much traffic the site gets and how much bandwidth the site uses. I also tend to toss in some stats about where the traffic comes from and what that traffic looks like.
That’s not all that fun and can be a pain to write.
So, let’s get that out of the way…
February wasn’t as great but January was awesome. Last month saw a new level reached – where this site averaged more than 1000 visitors per day.
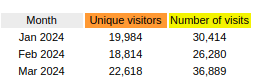
I guess the next major threshold will be when I get 1000 unique visitors in a month. Quite a few of you visit more than once, those are the ‘visits’ in the chart. The unique visitors are just that, how many unique people visit the site.
Sure enough, my traffic still comes from Google – even though I no longer use AdSense. As far as search traffic, the next two most popular search engines (for this site) are DuckDuckGo and StartPage.
The most popular operating systems are Linux, MacOS, and Windows. I suppose that makes some sense. Some of what’s on this site applies to MacOS as they’re a POSIX-compliant operating system.
The most popular browsers are Chrome (and those that identify as Chrome), Unknown, and Safari. Firefox isn’t well represented here. They’re 4th on the list with about 19% of my traffic.
My legitimate traffic comes from the United States, Germany, and the United Kingdom. China and Russia are in the stats, but they’re mostly bots. Finding accurate stats to pick between them can be difficult. So, the above is about what I can figure out.
Yeah, I regularly consume 50+ GB of traffic per month. Considering the site is pretty much pure text, that’s a lot of writing. There are millions of words on the site now and I’m still not out of ideas.
Anniversary!
This is our third anniversary! Three years!!! Whodathunkit?
This was the first article:
I’ve had some guest articles along the way (and at least another one coming when I can schedule it). Most of the articles, 99.999% at least, have been written by me.
We don’t get a lot of donations but we get a couple here and there. That helps cover the costs, plus people can now advertise here on the site. That’s helpful. I do love my CDN though it (and hosting) are expenses.
This has taken a whole lot of my time. I value my time, but I guess I also value the site. Otherwise, I’d have stopped publishing articles. One of these days I’ll quit but I plan on keeping up with the schedule for the time being.
That schedule? Well, you get a new article every other day. Most of those articles don’t contain any major errors, which is nice. I can’t be perfect all of the time, but I do my best. You’re welcome.
I’m working my way towards a million visits. That’s nice.
Here are the most popular articles:
How To: Remove AppArmor From Ubuntu
Change Between CLI and GUI Mode
How To: Disable Sleep And Hibernation on Ubuntu Server
Once upon a time, I was stoked to see 20 visits in a day. So, I guess I’ve built something here. Pardon me, but I’m a wee bit proud of my accomplishment. It has come a long way.
As such, I’m just going to keep this short.
Thank you. Thank you for your readership and encouragement. Here’s to another year. I think I’ve got another year of this in me. We’ll have to see. I’m bound to miss a day eventually, but this is three years without doing so (technically).
Closure:
That’s all, folks. I appreciate you.
Thanks for reading! If you want to help, or if the site has helped you, you can donate, register to help, write an article, or buy inexpensive hosting to start your site. If you scroll down, you can sign up for the newsletter, vote for the article, and comment.