In today’s article, we’re going to learn how to login to SSH to run one command. Yes, it’s another SSH article! However, this one should be relatively short. I’ve covered SSH a great deal already. This is just one more SSH trick.
SSH stands for Secure Shell and is a way to remotely control other computers. As I said in the opening paragraph, I’ve already covered a lot of SSH articles, because SSH is a tool I use regularly and it’s a tool I really like.
SSH lets me manage computers on the other side of the country without even leaving my chair. I also use SSH to manage various computers around my house. If I need to do something on a computer in another room, I can just SSH into it and do what I needed to do. It’s great!
Well, today’s SSH article is a bit different. We’re going to login to SSH to run one command. That’s all we’re going to do. We’ll login, automatically run the command, and then automatically exit the SSH connection. This is useful if you want to run a script, update, etc…
There are some previous SSH articles that you might want to read:
Install SSH to Remotely Control Your Linux Computers
Prevent SSH Root Login
Show Failed SSH Login Attempts
Alternatively, you can click to search for SSH articles. I’ve covered quite a bit of SSH material, so you can learn quite a bit from those links – even if you’re already familiar with SSH.
Well then, let’s just jump into the article… It really shouldn’t take long.
Login To SSH To Run One Command:
Like oh so many articles, and this one involving SSH, you’re going to need to start off with a terminal. You’ll also need a device that has SSH properly setup and ready to run. You can actually set SSH up on the computer you’re using and just SSH into localhost to practice this.
And, of course, if you don’t know how to open your terminal, just press
With your terminal now open, the format of the command is something like this:
1 | ssh <user>@<remote_device_address> '<command>' |
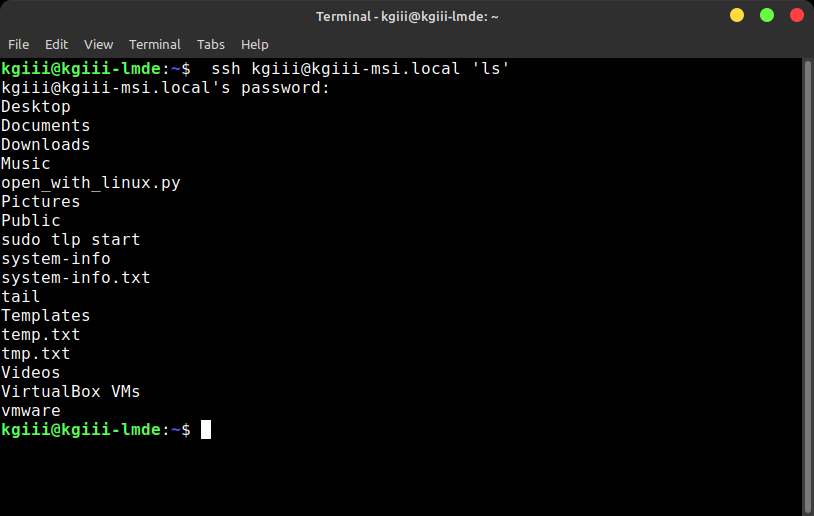
For example, if I wanted to connect via SSH to run one command, and that command was to list the files in the home directory, the command would look like this:
1 | ssh kgiii@kgiii-msi.local 'ls' |
Note: That device doesn’t face the public internet, so I don’t have SSH keys enabled on the device. So, that means I have to enter my password in the image below. With that in mind, the output of that command would look like this:
Of course, you can make it your own and there would be one less step if you had set up SSH keys. You can also make it more complicated if you want. You could try any one of the following commands, adjusting it for your needs:
1 2 3 | ssh kgiii@kgiii-msi.local 'cd ~/Downloads && ls -a' ssh kgiii@kgiii-msi.local 'my_script.sh' ssh kgiii@kgiii-msi.local 'sudo apt update && sudo apt upgrade -y' |
Go ahead and play around with this. If you want to login to SSH to run one command, that’s how you do it. You can make the command as simple or as complicated as you want. So long as you string it together properly, the sky’s the limit!
Like I said above, you can just install SSH on your single device and practice what you read in these SSH articles. It’s not particularly taxing. There are plenty of articles to help you along the way.
Closure:
See? It’s really not all that hard to login to SSH to run one command and then exit automatically after that command has been run. It’s another handy SSH trick that you can add to your SSH toolbox. Also, the article is longer than I anticipated. Ah well…
What comes next? I have no idea. I try to not write too many consecutive articles on the same subject. Mixing them up seems the best way to go about it, as the site’s meant to be searched and not read like a blog. I do have a bunch of SSH content, but I’ve also covered a whole lot of it already.
Thanks for reading! If you want to help, or if the site has helped you, you can donate, register to help, write an article, or buy inexpensive hosting to start your own site. If you scroll down, you can sign up for the newsletter, vote for the article, and comment.