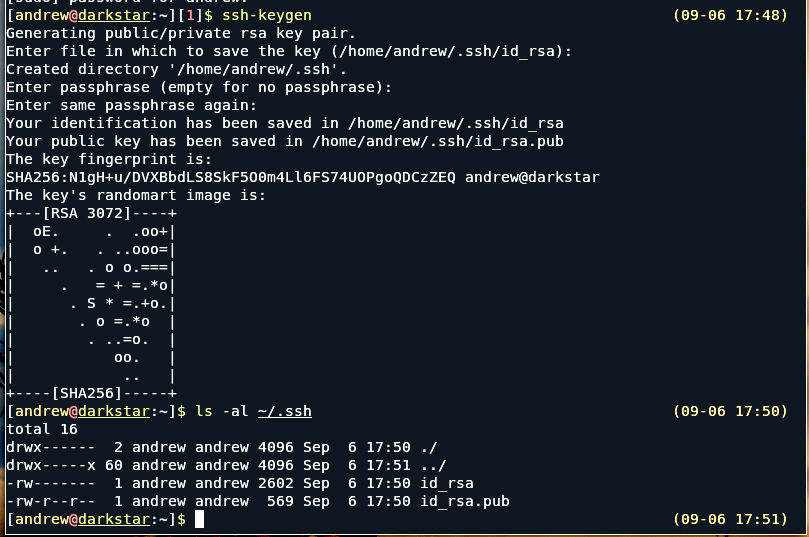
Today, we’re going to play with the ‘mv’ command, just as the headline implies. It’s a pretty easy command for anything you’re likely to do with it, and it’s a great way to accomplish some pretty neat things in the terminal.
So, let’s start with the ‘mv command. Right away, when we check the man page, it shows you one of its greatest features. It defines itself as:
mv – move (rename) files
And right away you see that it does more than just move files. It also seems to be a command that newer folks don’t use. Maybe they’re afraid of it? Maybe it just doesn’t get enough love? I dunno, but I know it’s a pretty great command. This article is gonna cover it.
Let’s mix things up a little! Why don’t you open your terminal and we’ll start from the same page. Enter the following commands into your terminal, one after the other, pressing enter between each one.
1 2 3 4 5 | cd ~/Documents mkdir tmp cd tmp mkdir test touch file1.txt file2.txt file3.txt |
Now, assuming I’ve done that properly and you’ve followed along, you should have made some files, a couple of directories, and your ‘pwd‘ (print working directory) is ~/Documents/tmp.
See? Now we’re all on the same page, and this is a fine time to start an article about the ‘mv’ command!
Play With The ‘MV’ Command:
So, for once, I don’t have to start this section by telling you how to open your terminal! You should have it open from the preparation we did in the intro! That’ll save some time…
So, with that terminal open, I want you to enter the following:
1 | mv file1.txt ./test |
That should move the ‘file1.txt’ to the test directory. If you want to actually verify this, just go like:
1 2 | cd test ls |
Which should show you that the file has in fact been moved. Let’s go back to that same tmp directory and verify that it’s no longer there.
1 2 | cd .. ls |
And you’ll see that file1.txt is no longer there in the tmp directory. And, seeing as you’re back in the right directory, let’s rename a file using the ‘mv’ command. Try this:
1 | mv file2.txt changed.txt |
This will have renamed the file2.txt to changed.txt and you can once again verify that the former has been renamed to the new filename changed with the ls command.
Finally, with one more trick up its sleeve, you can both change the name and move the file at the same time. To do so, you’d just go with:
1 | mv file3.txt ./test/changed-again.txt |
If you then run ls in both the pwd and test directory, you’ll see all the changes have been made, exactly as intended. If you need to, open your graphical file manager and verify it visually, but you can just as easily use the ls command and verify it all.
For fun, if you want to delete all those, you can move to the ~/Documents directory (cd .. or cd ../..) and use this command:
1 | rm -rf ./tmp |
That’ll clean up any sign that we’d been there and done this exercise. There’s more to the ‘mv’ command and, as always, be sure to check the man page for more usage instructions (to learn things like the -f switch). But, these are the most common ways you’ll use the ‘mv’ command and I wanted you to have a basic familiarity with it.
Closure:
And there you have it… It’s something a little different, as I felt it important that we start from the same place. I also figured I’d try a little bit of a different writing style for this one. If I can’t have fun, why do it? Either way, it’s yet another article. It’s one step closer to the year-long commitment I’ve made. (It’s gonna be a long year.)
Thanks for reading! If you want to help, or if the site has helped you, you can donate, register to help, write an article, or buy inexpensive hosting to start your own site. If you scroll down, you can sign up for the newsletter, vote for the article, and comment.