This article will show you a few ways to determine which distro and version you’re using. There are many ways to learn this, but these are three easy ways to tell.
There are any number of reasons why you might not know this information off the top of your head. Perhaps you’re working in a multi-platform job? You might have many devices. It’s possible that you may have a bunch of virtual machines, each different. One can’t always tell by just looking at the desktop, especially if you’ve done any customizing.
Additionally, you may have upgraded and not know things like the point release. You may have different versions across your network, each for its own purpose. You might just be forgetful and so you’ll need to determine the distro you’re using, as well as which version of that distro you’re using. You might be in a position where you need support, and being able to share this information is essential.
No worries, there are a few easy ways to determine which distro you’re using. All of them are pretty easy.
Determine Which Distro (and Version):
All of these methods will rely on the terminal. So, before you begin, you can open your default terminal emulator by using your keyboard and pressing
Once you have that open, you can try any combination of the following:
Method #1
The first method will involve a program known as ‘neofetch‘. Many distros actually provide this by default. If not, it’s probably in your default repositories and you can install it pretty easily. For example, with a Debian-based, or APT-using distro, the command to install it would be:
1 | sudo apt install neofetch |
Once installed, you can simply run it with the name of the application. No modifiers are required. You simply run:
1 | neofetch |
You’ll get an output similar to:
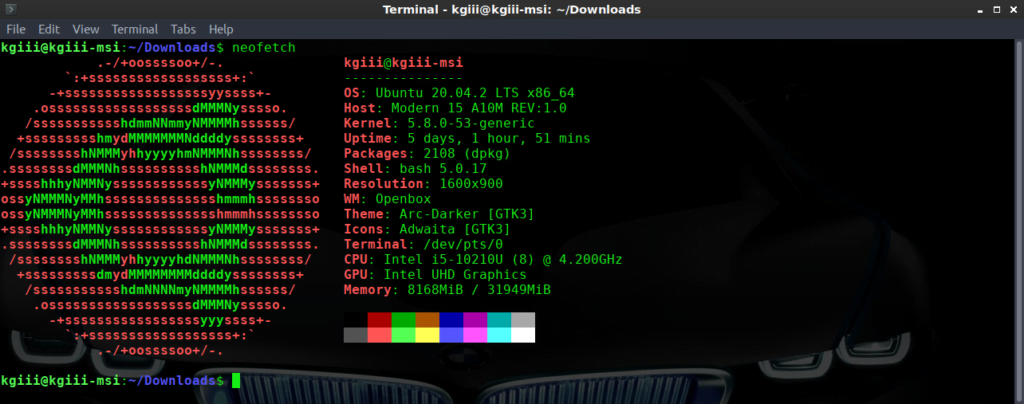
See? Nice and easy. The information to determine which distro you’re using is right there in the output and on the top-most line.
Method #2
The following two methods need no additional software. You simply need to run the command in the terminal.
The first of these two methods is:
1 | lsb_release -a |
Which will give you an output similar to:
1 2 3 4 | Distributor ID: Ubuntu Description: Ubuntu 20.04.2 LTS Release: 20.04 Codename: focal |
Again, this is self-explanatory. The top-most is the major name, the second is the version, then the release number, and then the codename. With this information, you can determine which distro you’re using.
Method #3
Your distro may not have any LSB data and may not contain that information. That’s okay, there’s still one more command for you to try. Again, you don’t need to install anything, it just works out of the box.
This time, the command you’ll be running will be ‘cat’ and you’re looking for release data in the /etc directory. The command looks like this:
1 | cat /etc/*release |
Your output should look similar to this:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 | DISTRIB_ID=Ubuntu DISTRIB_RELEASE=20.04 DISTRIB_CODENAME=focal DISTRIB_DESCRIPTION="Ubuntu 20.04.2 LTS" NAME="Ubuntu" VERSION="20.04.2 LTS (Focal Fossa)" ID=ubuntu ID_LIKE=debian PRETTY_NAME="Ubuntu 20.04.2 LTS" VERSION_ID="20.04" HOME_URL="https://www.ubuntu.com/" SUPPORT_URL="https://help.ubuntu.com/" BUG_REPORT_URL="https://bugs.launchpad.net/ubuntu/" PRIVACY_POLICY_URL="https://www.ubuntu.com/legal/terms-and-policies/privacy-policy" VERSION_CODENAME=focal UBUNTU_CODENAME=focal |
As you can see, that contains a ton of information, including where to go for support and where to file bugs.
Closure:
One of those is bound to work for you. I checked across a number of virtual machines and was able to determine which distro each was using. In many cases, all three of them will work for you.
At the end of the day, you can probably just pick your favorite (or the one that works) and commit it to memory. Personally, I try the ‘lsb_release -a’ first, as that one is firmly locked in my memory.
Like always, thanks for reading. I love the feedback folks provide, either here or at one of the sites I frequent. You may have noticed that I am now the owner/moderator of the LinuxTips Reddit Sub. If you frequent Reddit, and you’re interested in helping out, just drop me a note on Reddit and I’ll get you set up as a moderator there.
Of course, you can also unblock the ads used here. You can sign up for the newsletter. You can donate or write an article. There’s a few ways you can help keep this site going, or show your support. I currently write a new article every other day, though I’ve been considering increasing the frequency. Either way, let me know in the comments what you think of any of this stuff. I’m always curious about your thoughts regarding this site.