Today’s article is going to teach you how to use ‘netstat’ to find out what process is listening on a specific port. If you have open ports and don’t know why – and what’s listening on that port, you’re not making good security choices.
Let’s say you followed an article about how to monitor TCP/UDP in real time. If you’re new, or even just not all that advanced with Linux and networking, you might not know why there are all those ports and all that activity. Well, one of the things you should know is how to identify what process is listening on a specific port.
There are a number of ways to do this, but we’ll be using ‘netstat’. The ‘netstat’ application can be pretty advanced, but what we’ll be doing is pretty straightforward. If you’re curious, ‘netstat’ defines itself thus:
Print network connections, routing tables, interface statistics, masquerade connections, and multicast memberships
As you can see, it’s a pretty advanced application. It has a rather expansive man page, and we’ll largely ignore that as we really only need some limited functionality. All we really need to do, for this exercise, is find out what process is listening on a specific port.
With that in mind, let’s leap into the meat of the article…
What Process Is Listening On A Specific Port:
This article requires an open terminal. If you don’t know how to open the terminal, you can do so with your keyboard – just press
Once you have that open, you’ll need to find out if you have ‘netstat’ already installed. There are many ways to do this, I prefer:
1 | which netstat |
If you do not have ‘netstat’ installed, it’s certainly available for all mainstream distros and easily installed from your default repositories. Here’s how to install on a few distros:
Debian/Ubuntu/Mint/etc:
1 | sudo apt-get install net-tools |
RHEL/CentOS/Fedora/Rocky Linux/etc:
1 | sudo dnf install net-tools |
SUSE/OpenSUSE/etc:
1 | sudo zypper install net-tools |
If you’re using a different distro, root through the default repositories. It’s a pretty common tool and I’d like to imagine it’s easily available to anyone.
Once you have ‘netstat’ installed, the command we’re going to use is really, really, simple. In fact, I wrote this whole darned article mostly for just one command. I probably could have made it shorter. Still, it might as well be long enough to give some extra information along the way.
Anyhow, the command you run is this:
1 | sudo netstat -ptnl | grep -w ':<port_number' |
For example, you might have an open port 22 and want to know what process is listening on that specific port. So, you’re command would look like this:
1 | sudo netstat -ptnl | grep -w ':22' |
The end result will look something like this:
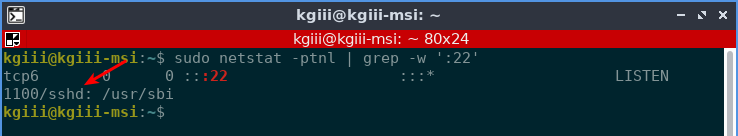
It may not be completely clear, but you can use this to deduce what process is listening on a specific port. If it’s not completely clear, you can get actually dig a little deeper. See the “1100” in there? Well, that’s the PID (Process ID) and you can use the following command to get more informtion. It looks like this:
1 | ps -p <PID> -o comm= |
The output from that in this case is:
1 2 | kgiii@kgiii-msi:~$ ps -p 1100 -o comm= sshd |
Which, as we know, is the daemon for SSH and thus nothing unexpected is running on port 22. See? Security!
Closure:
And there you have it, another article. This one is a pretty handy one, especially for when you want to know what process is listening on a specific port. If you have things running that you can’t identify, you can always stop by Linux.org and ask for help. Someone there will try to find out what’s going on for you.
Thanks for reading! If you want to help, or if the site has helped you, you can donate, register to help, write an article, or buy inexpensive hosting to start your own site. If you scroll down, you can sign up for the newsletter, vote for the article, and comment.