In today’s article, we’re going to learn how to control your WiFi with ‘rfkill’ and we’ll be learning a bit more than that. I think you’ll find ‘rfkill’ to be a nifty and useful terminal-based command to learn. Is this article appropriate for a beginner? Maybe? Maybe not? I’ll do my best to make it approachable for anyone at any level.
By the way, I’ve decided to intersperse the articles about simple commands like ‘lsusb’. I don’t want to bore my more advanced readers – and I don’t want to bore myself. I’ve decided to make the time necessary, even though I’m pretty busy. I’ll be busy for a little more than a week. (Ask me in private, if you want.)
Anyhow, you should learn about ‘rfkill’, as it’s a pretty handy tool for controlling your wireless. If you look at the name, there should be some indication that it’s actually more than just WiFi. You can use ‘rfkill’ to manage Bluetooth, for example. Bluetooth is also wireless communication. As such, you can use ‘rfkill’ to manage that as well.
So, what is ‘rfkill’? Let’s see how the man page defines it:
rfkill – tool for enabling and disabling wireless devices
See? It says what you’d expect, assuming you read the previous paragraph. The title only mentions WiFi, but that’s really due to space and convenience. You can use ‘rfkill’ to manage both WiFi and Bluetooth. Pretty handy, huh?
Well then, let’s just get the party started…
Control Your WiFi with ‘rfkill’:
Sure enough, you use ‘rfkill’ in the terminal. On Linux-Tips.us, we do a whole lot of stuff in the terminal. So, open your terminal now. If you don’t know how to open your terminal, just press
With your terminal now open, let’s first gather some information:
1 | sudo rfkill -o ID,TYPE-DESC,SOFT,HARD |
The output should look a little bit like this, or a lot like this:
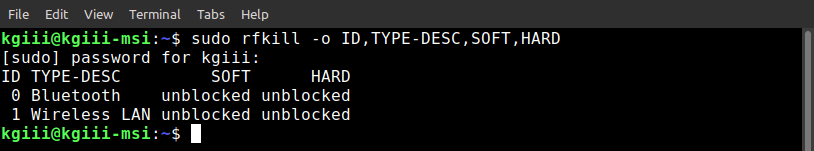
The information you’re after “ID,TYPE-DESC,SOFT,HARD” is easy to understand.
The first column is the ID number and the second column is a description of the device. The third column is if there’s a ‘soft block’ on the device, and the fourth column is if there’s a ‘hard block’ on the device.
If you see a ‘soft block’, that’s when there’s some software that disabled the device. A ‘hard block’ is when there’s a hardware block on the device. If it is soft blocked, you’ll need a software solution to turn it on – like ‘rfkill’.
Additionally, when you see a ‘hard block’, it means there’s probably a physical switch (often an
Importantly, the ‘rfkill’ application can do nothing about a hard block. But, it can do something about a soft block. If you want to unblock WiFi, try this:
1 | sudo rfkill unblock <ID> |
Using my computer’s output, to unblock the WiFi the command would be:
1 | sudo rfkill unblock 1 |
You can also unblock with the description. To unblock the WiFi with the description looks like:
1 | sudo rfkill unblock wireless |
Of course, you can also do the opposite. Instead of ‘unblock’ you would use ‘block’. That means the opposite of the above command would be:
1 | sudo rfkill block wireless |
If you want, you can also just ‘toggle’ the devices. When you toggle it, it turns off if it was on – and it turns on if it was off. You do that with the ID. If I wanted to toggle the wireless, the command would look like:
1 | sudo rfkill toggle 1 |
That will turn my WiFi off (if it was on) or it will turn my WiFi on (if it was currently turned off). See? It’s pretty simple!
Well, I hope I’ve made it simple. If it’s not simple, I hope it’s at least approachable. Like always, feel free to drop a question as a comment. If I don’t have an answer, I’ll try to direct you to someone who does.
Also, don’t be afraid of the man page. There’s a lot more to ‘rfkill’ than I’ve covered in this article. We’ve mostly just scratched the surface. To check the man page:
1 | man rfkill |
That’ll give you all the information you want. Plus, I’m sure others have authored pages that will go into more depth. We tend to not do too much of that here. I just want you to be up and running, not Linux gurus. If you want to be a Linux guru, you’ll need a whole lot more than just this site!
Closure:
Well, I’m glad you made it through today’s article. I tried to keep it nice and simple, simply showing you a way to control your WiFi with ‘rfkill’. But, there’s more to it, including Bluetooth. I like to think I’ve made this approachable for even a new user, but maybe not…
Again, feel free to comment about this. Is it easy enough for a new person? How about a new person coming from a Google search? Is it easy enough for a novice, someone completely new to computers? (Probably not, but let me know what you think. Thanks!)
Thanks for reading! If you want to help, or if the site has helped you, you can donate, register to help, write an article, or buy inexpensive hosting to start your own site. If you scroll down, you can sign up for the newsletter, vote for the article, and comment.