In today’s article, we’re going to learn another way to scan a remote host for open ports. It’s actually going to be an easy article to follow, suitable even for beginners. Read on, I promise it’s not all that complicated! We can make this pretty simple.
There are a couple of reasons why you’d want to scan for open ports. You may want to know what ports you have open, or you may be interested in penetrating a remote host and want to know what ports are open (and things like what services are running on them).
This may seem a little familiar. We recently used the ‘nc’ command to check if a specific port is open. You can (and should) read that article (it goes into describing ports, so it’s worth reading as I don’t want to duplicate the work) here:
How To: Check If A Specific Port Is Open
Again, if you’re not all that familiar with ports, you should read that article. It explains them in more detail.
The tool we’re going to use is ‘nmap‘, a familiar tool that’s used by security professionals, but can be used for our purposes just fine. It’s not all that daunting, which is why I feel even a beginner can learn to scan a remote host for open ports.
Installing nmap:
Alas, nmap is seldom installed by default. As such, you’ll need to install it. We’ll do that in the terminal. If you need to open a terminal, just press
So, let’s get nmap installed:
Fedora/Derivatives:
1 | sudo dnf install nmap |
Debian/Ubuntu:
1 | sudo apt install nmap |
RHEL/CentOS:
1 | sudo yum install nmap |
I know those should work, but nmap will certainly be in most default repositories. You should be able to install it with your package manager. Once you have nmap installed, you can check the man page to see how nmap describes itself:
1 | man nmap |
There, you’ll see:
nmap – Network exploration tool and security / port scanner
Which, as you can guess, is a pretty good description. You’ll also notice that there are a whole lot of options. It’s a pretty complicated command. Don’t worry, we’ll make it easy for our goal, which is too…
Scan A Remote Host For Open Ports:
You should have an open terminal from the previous section. You’ll need that. While there are graphical tools for scanning for open ports, nmap is not one of them. You use nmap in the terminal, like so many of the great Linux applications.
So, then let’s start with the basics. If you want to scan a remote host for open ports, your best starting point will be:
1 | nmap <remote_host> |
For example, you could use Linux-Tips.us as a test:
1 | nmap linux-tips.us |
Or you can use a computer on the same network via the hostname or IP address. That’d look like:
1 | nmap kgiii-msi.local |
However, that command won’t actually scan all the possible ports. It only scans the 1000 most common ports, which is usually what you’re after. You can scan the entire range of ports if you want. That’d look like:
1 | nmap -p- <remote_host> |
If you want, you can actually scan for a specific port to see if that port is open on the remote host. That’s a bit more complicated, but not much. Try a command that looks like this:
1 | nmap -Pn -p <port_number> <remote_host> |
To try to make that more clear, see the following example to check to see if the default SSH port is open:
1 | nmap -Pn -p 22 kgiii-msi.local |
I’ve even made you an example image of the above commands:
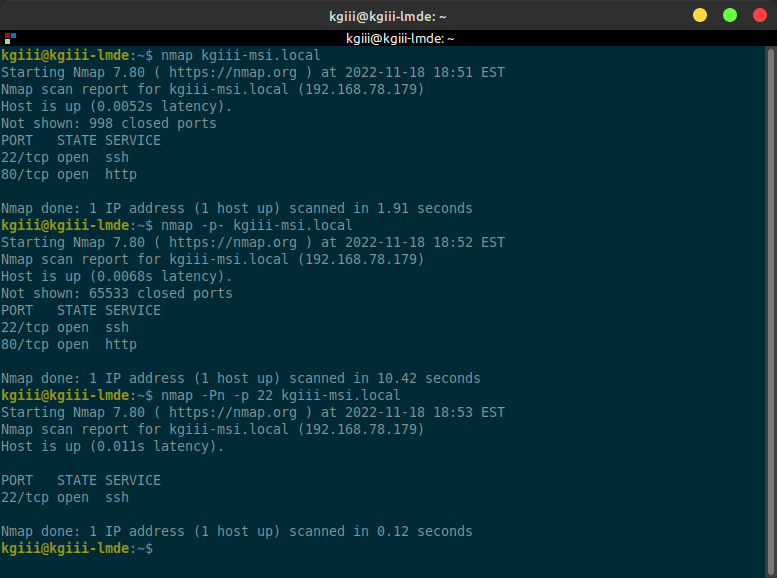
See? While nmap may seem daunting when you first check the man page, it’s pretty easy to use nmap to scan a remote host for open ports. It’s even easy enough for a newbie to use!
Closure:
Well, that’s another article. I have yet to run out of notes and I have yet to run out of ideas for articles. So, there are likely to be even more articles written. Eventually, I’m sure to run out – or need a break. But, for now, you have an article that tells you how to scan a remote host for open ports. It’s even easy enough for a beginner.
The nmap application is one of the first tools you’ll learn when you decide to learn about network security. If you want to probe a site for security holes, it’s important to know which doors are open and available for you to explore. Well, that’s where tools like nmap come into play and this article will get you started.
Thanks for reading! If you want to help, or if the site has helped you, you can donate, register to help, write an article, or buy inexpensive hosting to start your own site. If you scroll down, you can sign up for the newsletter, vote for the article, and comment.