This article is a bit of a review of some software called ‘uMatrix’. If you’ve never heard of it, it’s an impressive piece of software – especially considering it’s a browser extension.
I was nosing around some old projects in my GitHub when I decided to look upstream. Lo and behold, Ray Hill (gorhill of uBlock Origin fame) has picked up developing uMatrix again. (Install through your browser’s extension manager. Links below.)
What is uMatrix? GitHub page here.
Well, do you remember old school firewalls where you could not just block things by application, you could be even more refined – like narrowing it down to which port, ingress or egress, and even which domains that application could connect with?
Imagine something similar to that, except it’s for your browser. For each page, you can elect to block images, CSS, cookies, scripts. Then, you can decide which scripts and which CSS to allow through. You can elect which third party assets load, from cookies to images – and you can do so on a domain name basis.
There’s a learning curve. It’s a pretty big learning curve for a browser extension. Plan on a couple of hours to really get used to it – and to get your favorite sites configured. You need only configure them once and then you can backup the settings so that you can use it on multiple devices or put it aside for safekeeping.

More About uMatrix:
If I took privacy serious and were more security focused, I would not use the internet without uMatrix. As it stands, I have an older version (now updated) configured in one browser for when I want to visit stuff I absolutely don’t trust. If you take privacy serious (and cross-domain scripting, third party cookies are a huge no-no, but so shouldn’t images and CSS files) then you really, really should take a look at this extension.
Take a look at this:
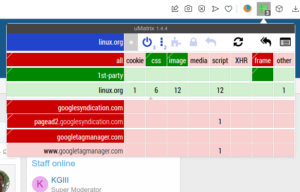
In each of those columns, you can click to block it everywhere or to allow it on this one specific domain. As you can see, there’s everything from cookies to CSS, from media to scripts. The refinement you can achieve is amazing. It will take some work and time for you to ‘get good’ with uMatrix.
Now, you basically want it to operate in the default configuration you have it in right after installing, only allowing CSS and images from the domain you’re visiting.
When a site refuses to work properly, you can start by allowing scripts on an individual basis – on the per-site basis you see from the domains listed on the left. You can click on two areas in each column to give fine-grained permissions. After a while, you can get pretty quick at deducing why it doesn’t work. It’s usually a script from another site that needs to be enabled.
You’ll also learn how much cruft the web has, browsing much faster and having fewer scripts chew up your CPU and RAM. If you have a low-end computer, this is also a must-have.
At one point, Hill had stopped working on the project and shuttered it. I’m not sure when he started working on it again. I’m glad they did because it’s the best privacy and security browser extension I’ve ever seen in my life. Now that he’s working on it again, I feel comfortable recommending it.
uMatrix Review:
Really, I wrote this to share my joy. If I had to review it, and I guess I have to, I’d give it a solid 9.5 out of 10. I’ve deducted a half point because there’s no effort to make it all that intuitive to new people and this makes the learning curve harder. It’s hard to explain, but once you see what it does you will understand it better.
Not even I can make it all that intuitive until you actually test it out and start browsing the web with it. If you get frustrated, settle down and relax. You can make it work. It will take some time to get used to the new paradigm. You can browse much faster (more so than from just blocking ads) when you’re not loading a bunch of 3rd party cruft.
You might as well know where to get it. It’s available for the two major browsers, plus in Opera’s own little extension store. These extensions work fine on same-family browsers, like Pale Moon or Google Chromium.
You can pick it up for Opera here.
Of course, you can pick it up for Firefox here.
And you can pick it up for Google Chrome here.
Give it a shot. Commit to browsing with it for a full day and see for yourself what the web is like when you’re not loading tracking cookies, scripts, ad images loaded from other domain names, and so much more.
By the way…
I worried more about these things years ago, back when I was a Windows user and for the times when broadband wasn’t a realistic option. I was more concerned with my security and letting scripts load in the browser, so I’d use uMatrix. It had the added benefit of doing a great deal to protect my privacy by making it extremely difficult to track my movements across the web. These days, browsers are much more secure and run in their own containers and I care less about privacy.
Even just blocking remote scripts, media, and images will speed up your browsing noticeably. By the time you have it configured for the sites you visit, you’ll have a pretty secure and private browsing experience. You should also consider making it work in incognito mode if you make regular use of private browsing.
Closure:
There you have it, another article. This one is a review of uMatrix, one of my favorite browser extensions even though I don’t actually bother with it for most of my browsing. I used to browse with it exclusively, but I’ve given up caring. If you care, and many of my readers do, then I highly recommend trying it for a full day. Commit to a full day and then leave a comment telling us of your experiences.
Thanks for reading! If you want to help, or if the site has helped you, you can donate, register to help, write an article, or buy inexpensive hosting to start your own site. If you scroll down, you can sign up for the newsletter, vote for the article, and comment.